How to Choose the Right Security Access Control System for Your Business
In the ever-evolving landscape of business security, selecting the right Security Access Control System is paramount for maintaining operational integrity and protecting sensitive information. According to a report by MarketsandMarkets, the access control market is projected to grow from $9.2 billion in 2020 to $13.0 billion by 2025, highlighting the increasing importance of robust security measures in various sectors. The report also emphasizes that businesses are increasingly adopting advanced access control technologies to mitigate risks associated with unauthorized access and data breaches.
Industry expert Dr. Emily Carter, a leading voice in security technologies, articulates the essence of this choice by stating, "A well-implemented Security Access Control System not only safeguards physical spaces but also fortifies the trust that clients place in your business." As organizations confront escalating threats and integrate more digital solutions, the demand for customized and scalable access control systems continues to rise. This underscores the necessity for businesses to carefully evaluate their specific security needs and opt for solutions that not only address current challenges but also anticipate future demands.

Understanding the Importance of Security Access Control Systems
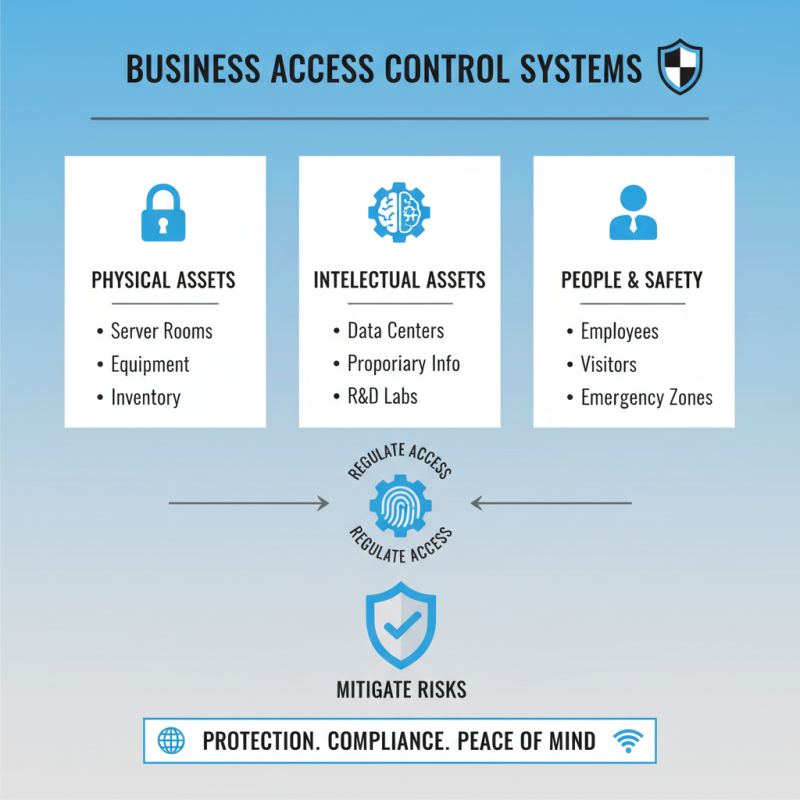
Security access control systems play a crucial role in safeguarding a business’s physical and intellectual assets. By regulating who can enter specific areas within a facility, these systems help mitigate risks associated with unauthorized access. In today’s evolving security landscape, the importance of these systems cannot be overstated. They not only protect sensitive data and valuable equipment but also ensure the safety of employees and clients within the premises.
Implementing a robust security access control system fosters a secure environment that can adapt to particular needs. For instance, businesses can set varying access levels for employees based on their roles, enabling greater oversight and accountability. Additionally, advanced features such as surveillance integration, real-time monitoring, and reporting capabilities enhance an organization’s ability to respond to potential threats proactively. As security threats continue to evolve, understanding and investing in the right access control system is essential for maintaining a safe and secure business environment.
Evaluating Your Business's Unique Security Needs
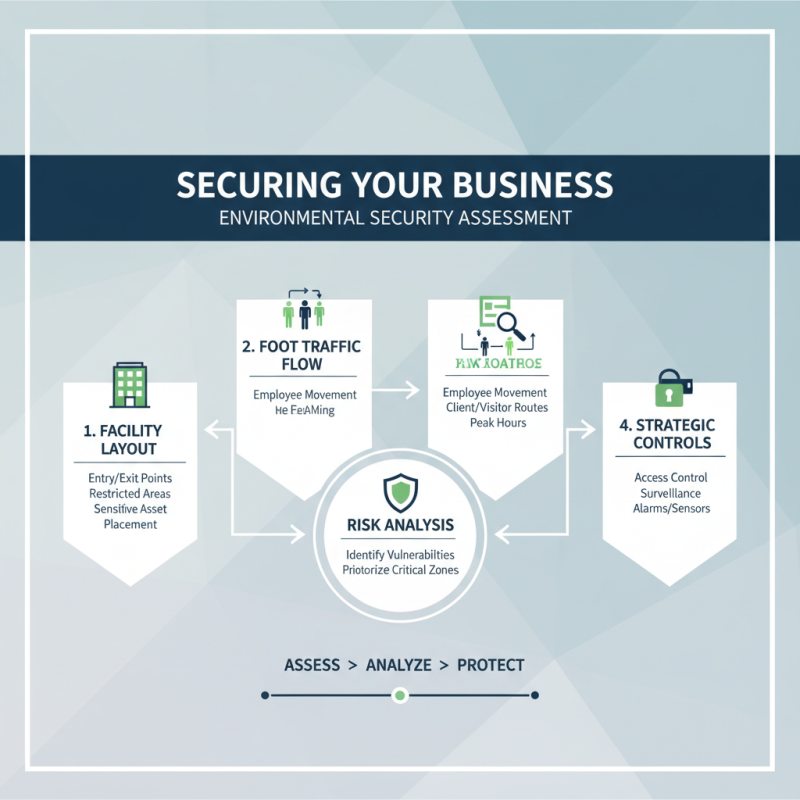
When evaluating your business's unique security needs, the first step is to conduct a thorough assessment of your environment. Consider the layout of your facilities, including entry and exit points, areas of restricted access, and the placement of sensitive information or valuable assets. This assessment should also account for the flow of foot traffic, as understanding how employees, clients, and visitors move through your space can inform decisions about where access control measures are most critical.
Next, identify potential security risks specific to your business. This may involve engaging key stakeholders to gather insights on past security incidents or reviewing industry-specific threats. For instance, a retail business may face theft, while a healthcare facility may prioritize patient privacy. Additionally, ensure that your access control system can accommodate your operational workflow while providing the necessary security features. Flexibility in user permissions and integration with existing security systems can enhance your overall protection and operational efficiency. By addressing these unique security considerations, you can select an appropriate access control system that effectively mitigates risks and safeguards your business.
Types of Access Control Systems: Pros and Cons
When selecting the right access control system for your business, understanding the various types available can significantly inform your decision. One of the most common types is the card-based access control system, which allows employees to enter secured areas using ID cards or key fobs. The main advantage of this system is its ease of use and ability to integrate with other security measures. However, there are drawbacks, such as the potential for lost or stolen cards, which can compromise security if not managed properly.
Another option is biometric access control, which utilizes unique physical characteristics such as fingerprints or facial recognition. This system offers enhanced security since it is difficult to replicate an individual’s biometrics. Nevertheless, the costs associated with biometric systems can be higher than traditional methods, and there may be privacy concerns from employees regarding the collection and storage of personal data.
Lastly, mobile access control systems are gaining popularity, allowing users to unlock doors using their smartphones. This modern approach provides convenience and flexibility; however, it is contingent upon reliable smartphone technology and internet connectivity, which may not always be guaranteed. Each type of access control system presents distinct benefits and challenges, making it essential for businesses to assess their specific security needs and operational environment before making a choice.
Key Features to Look for in a Security Access Control System
When selecting a security access control system for your business, there are several key features to consider that will ensure optimal protection. Firstly, look for a system that offers scalability. As your business grows, your security needs may change, so choosing a solution that can easily adapt to increased access points or additional users is crucial. Additionally, ensure that the system supports various access methods, such as keycards, biometrics, or mobile credentials, allowing flexibility for both staff and visitors.
Another important feature to look for is real-time monitoring capabilities. A system that provides live data tracking can help you respond promptly to any security breaches or unauthorized access attempts. Moreover, make sure the system includes comprehensive reporting tools, enabling you to analyze access patterns and identify potential vulnerabilities in your security framework.
Tips: When evaluating potential systems, prioritize user-friendly interfaces and robust customer support. A system that is easy to navigate will streamline operations for your team, while responsive technical support can save you time and stress when issues arise. Additionally, consider systems that offer integration with existing security measures you may have in place, such as surveillance cameras and alarm systems, for enhanced security coverage.
Budgeting and Cost Considerations for Implementation
When selecting a security access control system for your business, budgeting is a critical factor that can significantly influence the quality and scope of your implementation. According to a report by MarketsandMarkets, the global access control market is projected to grow from USD 8.6 billion in 2020 to USD 12.5 billion by 2025, highlighting a growing recognition of the importance of robust security solutions. Businesses must carefully assess their financial capabilities while considering the cost of hardware, software, installation, and ongoing maintenance.
Initial setup costs can vary widely, with basic systems starting around $3,000, while more advanced solutions can exceed $20,000 based on features and size of the implementation. The National Institute of Standards and Technology (NIST) emphasizes that a well-planned budget should also account for personnel training and potential future upgrades.
It is essential to calculate the total cost of ownership, which includes not just the upfront expenses but also the long-term operational costs. This comprehensive financial assessment can help businesses choose an access control system that aligns not only with their immediate security needs but also with their strategic vision for growth and sustainability.
Related Posts
-

Understanding Import and Export Certifications for Best Security Access Control Systems
-

2025 Top Security Access Control Systems: Innovations and Trends
-

Essential Access Control Panel Checklist: Your Key to Enhanced Security Management
-

Digital Innovations in Best Access Control Security Solutions
-

Ultimate Guide to Choosing the Best Access Systems for Your Global Procurement Needs
-

Unlocking Safety: A Comprehensive Guide to Innovative Security Access Control Systems
- • HighpowerOne Touchscreen Controller • HighpowerOne Mobile Credential App
- Highpower Management System
- • Pushplate 100 PNZ
- • Pushplate 110 PNZ
- • Pushplate 120/140 PNZ
- • Pushplate 130/150 PNZ
- • Pushplate 200 PNZ
- • Pushplate 100
- • Pushplate 110
- • Pushplate 120/140
- • Pushplate 130/150
- • Pushplate 200
Mechanical Timers
Proximity ID Access Cards and Fobs
Proximity Card Readers
- • Proximity Reader P-300
- • Proximity Reader P-400
- • Proximity Reader P-500
- • Proximity Reader P-620
- • Proximity Reader P-640
- • Proximity Reader P-710
- • Proximity Reader P-900
- • Ranger Proximity Readers
- • Ranger Controls
- • Sure-Fi Wireless Interfaces
Smart Series JX Readers
Electromagnetic Locks
Highpower Power Supplies
• H505
• H512
Security Products Summary
